Viruses and malware are a major threat to modern businesses. Systems and networks are vulnerable to malicious attacks, which can leave decision-makers with little recourse when things go wrong.
Targeted attacks require ransomware protection measures to ensure they are shut down fast. Businesses that invest in combating ransomware can protect their data and save money, giving stakeholders and clients a greater level of confidence.
There are many ways to protect critical data from malicious online activities. The use of basic web security protocols for ransomware protection can go a long way in reducing the potential for severe data breaches.
Application whitelisting, threat hunting and detection, and next-gen antivirus software will all help keep your business safe from potential attacks.
What Is Ransomware?
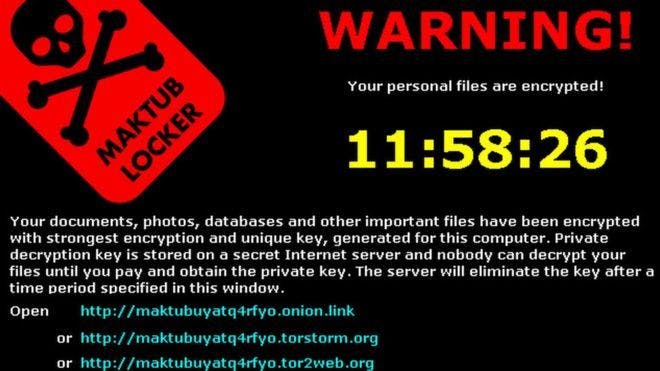
Ransomware is a form of extortion in which malicious actors lock users out of important data and demand money to restore access. They can also threaten to release private information. Ransomware attacks are used to hold data hostage for a specific period of time or until certain demands are met.
Generally, ransomware involves the encryption of files with an encrypted key that only the attackers have access to. Files will be made inaccessible until a sum is paid or victims agree to do something for the attacker. Critical data is leveraged against unsuspecting owners who have not properly invested in ransomware protection.
Ransomware can be a huge headache for IT departments that aren’t properly equipped with the tools and knowledge for prevention. It is a major threat, costing time and money when attacks occur. Ransomware protection will give your business an added layer of security, often preventing potential threats before they even arise.
Why Do Ransomware Attacks Occur?
Ransomware attacks occur for many reasons, including the theft of money, assets, or intellectual property.
Companies are often targeted due to the growth of improperly secured hardware, software, and networks. IT departments with holes in their infrastructure make data storage, processing, and transfer systems prime targets for ransomware attacks.
The occurrence of ransomware attacks is problematic for all types of organizations, including businesses, government agencies, and private institutions. Ransomware attacks can lead to major disruptions in critical operations, which can also have potential consequences for society.
Important infrastructure such as power stations, the electric grid, traffic lights, and security systems are vulnerable to such attacks. Ransomware protection creates a safer environment for operating vital infrastructure.
How Has Ransomware Evolved Over Time?
The evolution of ransomware over time has given rise to powerful tools that malicious actors can use to take over important systems. As the internet has continued to grow and begun to be used for more essential operations and transactions, ransomware has also changed and adapted to fit the environment.
At first, ransomware was primarily delivered through phishing and e-mails containing messages tempting users to click on malicious links or file downloads. As the internet became more visible, people started using more of the available antivirus apps and software.
This change in usage patterns gave rise to a growth in malware embedded in downloaded programs, including pirated and cracked software. As more people and businesses began connecting on the web, malicious actors began using social engineering to trick unsuspecting people into giving out login information.
Because devices are much cheaper and smaller now, it’s easy for ransomware to be placed on infected devices such as USBs and left for unwitting individuals to plug into their own systems.
Businesses should be careful, use ransomware protection, and have strict protocols in place for what equipment and software can be used, both internally and externally.
Application Whitelisting
Application whitelisting is essential to ensure users don’t accidentally infect vital systems. This protection involves defining which applications can be safely used.
The opposite of application whitelisting is application blacklisting. Blacklisting is when specific websites and programs are blocked after they are determined to be harmful. While blacklisting provides more user freedom, whitelisting is the more proactive, and therefore effective, approach.
Application whitelisting involves testing and screening a wide variety of software and developing tools that can identify potential threats.
Restrictions can be set to prevent individuals from using specific services without whitelisted applications. Restricting application usage to those applications that are verified to be safe is the first line of defense for many organizations.
Threat Hunting and Detection
Assessing the viability of internal security ecosystems is a necessary part of malware mitigation. The use of threat detection ensures any potential security vulnerabilities that occur will be quickly shut out of the system. Processes used to detect, identify, and remove potential threats are important for long-term security management.
Threat hunting assumes a threat has already entered the system and utilizes powerful tools to locate and eliminate those threats before they can cause problems. While application whitelisting serves as the first line of defense for businesses, threat hunting serves as the second in case a breach occurs.
Next-Gen Antivirus Software
Antivirus software is a vital line of defense for businesses that need ransomware protection. The use of applications that can detect and prevent viruses before they cause harm to the user’s system is important for warding off malware. Modern cyber security software uses the cloud to deliver next-gen antivirus capabilities to end-users.
Most antivirus software offers a more proactive approach to combating ransomware. Users can check for potential issues in real-time.
This level of availability makes it easier for businesses to keep up with the ongoing fight against ransomware attacks. Next-gen antivirus software provides ransomware protection with state-of-the-art cloud-based scanning and removal tools.
Ransomware Protection with ITSG
Data security and protection from potential malware threats are essential in today’s business world. ITSG provides IT support and services to businesses working in the cloud.
We provide reliable and affordable technology support and ransomware protection that makes it easier for you to leverage the power of the cloud to improve business performance without worrying about the risks. ITSG will improve your company’s productivity.
Don’t let your technology investments go to waste. Our real-world solutions get results. We offer practical IT support so that you can save money and get more done. ITSG will ensure better ransomware protection for your business.
Combat ransomware with ITSG. Call us today!